|
Designing Security for a Microsoft Windows
2000 Network When you pass this exam, you achieve
Microsoft Certified Professional status. You also earn credit
toward the following certifications:
Elective credit toward Microsoft Certified Systems Engineer
on Microsoft Windows 2000 certification
According to Microsoft,
"This certification exam tests the skills required to
analyze the business requirements for security and design a
security solution that meets business requirements. Security
includes:
Controlling access to resources
Auditing access to resources
Authentication
Encryption
"
The scale of the network environment we are talking about
in this exam are:
- Supported users range from 200-26,000+
- Physical locations range from 5-150+
-
Typical network services and applications
include file and print, database, messaging, proxy server or
firewall, dial-in server, desktop management, and Web
hosting.
- Connectivity needs include connecting individual offices
and users at remote locations to the corporate network and
connecting corporate networks to the Internet.
It is recommended that you first start by studying 70-215
and 70-216 to ensure that you are familiar with Windows 2000
network infrastructure.
This exam is CASE STUDY BASED. You should download and try
the Case Study-Based Test Demo available at
http://download.microsoft.com/download/vb50pro/Update/2.0/W9X2K/EN-US/IIT_Demo.EXE
to become familiar with these new types of questions before
taking the exam.
You must know how to:
To succeed in case study
questions, the planning and deployment theories are as
important as the underlying technical contents.
Before you proceed…
Study the following topics thoroughly before proceeding on
220. The following topics are available in 215, 216 and 217.
-
Authentication
-
Auditing
-
Security Templates
-
Security Policies
-
PKI
-
VPN
Security Concepts
considerations
Windows 2000 deploys
distributed security strategies.
The seven primary security
strategies to pursue in making your network resources secure
are:
- Authenticate all user access
to system resources.
- Apply appropriate access
control to all resources.
- Establish appropriate trust
relationships between multiple domains.
- Enable data protection for
sensitive data.
- Set uniform security
policies.
- Deploy secure applications.
- Manage security
administration.
Below are the relevant concepts you must bear in mind:
- Security Model
- Domain Model
- Trust Management
- Security Policy
- Security Configuration and Analysis
- Symmetric Key Encryption
- Public Key Encryption
- Authentication
- Single Sign-On
- Two-Factor Authentication
- Access Control
- Data Integrity
- Data Confidentiality
- Nonrepudiation
- Code Authentication
- Audit Logs
- Physical Security
- User Education
Physical Security and User Education are often ignored. In
fact, they are HIGHLY CRITICAL.
"A critical factor for ensuring the success of your
network security staff is to be sure they are well trained and
kept up-to-date as technologies change. The staff needs to
take time to learn Windows 2000, particularly its network
security technologies. They also need to have opportunities to
reinforce their training with experimental work and practical
application."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgfb_emp_guod.htm
Policies and procedures are important too. We are not
talking about the technical polices in Windows 2000. We are
talking about the office policies that are related to business
security:
"Policies and procedures are always important, but they
are critical for security. You need to create and publish your
policies to gain consensus on how you will handle specific
security issues and to ensure that everyone clearly
understands the policies. Formalized procedures ensure that
system maintenance and changes are always done in a
well-thought-out manner."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgfb_emp_yjxu.htm
As a security professional,
you will need to go through the steps listed in the task list
below:
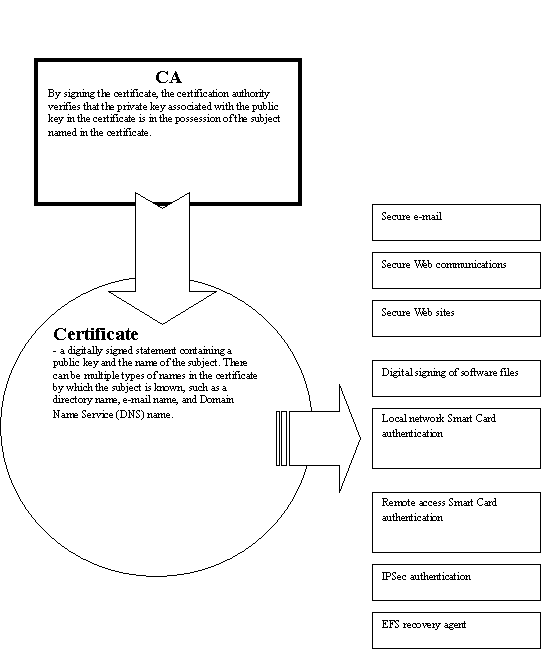
Your security plan should
include the following sections:
* this table is extracted from the Microsoft technical web
page at
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgbe_sec_orhf.htm
:
|
Sections in the Plan |
Description |
|
Security risks |
Enumerates the types of security hazards that affect your
enterprise. |
|
Security strategies |
Describes the general security strategies necessary to
meet the risks. |
|
Public key infrastructure policies |
Includes your plans for deploying certification
authorities for internal and external security features. |
|
Security group descriptions |
Includes descriptions of security groups and their
relationship to one another. This section maps group
policies to security groups. |
|
Group Policy |
Includes how you configure security Group Policy settings,
such as network password policies. |
|
Network logon and authentication strategies |
Includes authentication strategies for logging on to the
network and for using remote access and smart card to log
on. |
|
Information security strategies |
Includes how you implement information security solutions,
such as secure e-mail and secure Web communications. |
|
Administrative policies |
Includes policies for delegation of administrative tasks
and monitoring of audit logs to detect suspicious
activity. |
The security risk metrics:
* this table is extracted from the Microsoft technical web
page at
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgbe_sec_nlhn.htm
|
Security Risk |
Description |
|
Identity interception |
The intruder discovers the user name and password of a
valid user. This can occur by a variety of methods, both
social and technical. |
|
Masquerade |
An unauthorized user pretends to be a valid user. For
example, a user assumes the IP address of a trusted system
and uses it to gain the access rights that are granted to
the impersonated device or system. |
|
Replay attack |
The intruder records a network exchange between a user and
a server and plays it back at a later time to impersonate
the user. |
|
Data interception |
If data is moved across the network as plaintext,
unauthorized persons can monitor and capture the data. |
|
Manipulation |
The intruder causes network data to be modified or
corrupted. Unencrypted network financial transactions are
vulnerable to manipulation. Viruses can corrupt network
data. |
|
Repudiation |
Network-based business and financial transactions are
compromised if the recipient of the transaction cannot be
certain who sent the message. |
|
Macro viruses |
Application-specific viruses could exploit the macro
language of sophisticated documents and spreadsheets. |
|
Denial of service |
The intruder floods a server with requests that consume
system resources and either crash the server or prevent
useful work from being done. Crashing the server
sometimes provides opportunities to penetrate the system. |
|
Malicious mobile code |
This term refers to malicious code running as an
auto-executed ActiveX® control or Java Applet uploaded
from the Internet on a Web server. |
|
Misuse of privileges |
An administrator of a computing system knowingly or
mistakenly uses full privileges over the operating system
to obtain private data. |
|
Trojan horse |
This is a general term for a malicious program that
masquerades as a desirable and harmless utility. |
|
Social engineering attack |
Sometimes breaking into a network is as simple as calling
new employees, telling them you are from the IT
department, and asking them to verify their password for
your records. |
Defining realistic security
goals
Examples of realistic communication and information
security goals as suggested by Microsoft:
The key to establish a proper goal is to ensure that it is
realistic:
"Setting unrealistic security goals (for example,
specifying an unnecessarily high level of security) can result
in security requirements that cost too much to implement or
maintain. Unrealistic security goals can also exceed the
limits of existing technology and performance capabilities."
Microsoft Reskit
Estimate the risk of attacks
on your network resources
Risk of attack and subsequent compromise of a system is
affected primarily by the following factors:
- How secure your network is from external and internal
attacks.
- If your networks are connected to the Internet, there
is always some risk of external attack
- If you lack adequate firewall and proxy services, the
risk of external attack is very high.
- If workstations and servers are stored in secure
locations, the risk of internal attack is usually
relatively low.
- If unauthorized users have access to workstations or
if network servers are not stored in secure data centers,
the risk of internal attack is much higher.
- How valuable your network resources are to attackers.
- How high the cost of an attack is to the attackers. As
stated by Microsoft:
"In general, only attackers that have cryptanalysis
equipment and skills, a significant incentive to launch the
attack, and considerable time to invest in the attack choose
to pursue costly attacks on resources that are protected by
strong cryptographic security technology."
Considerations when
determining Windows 2000 Network Security Strategies
- In many cases, Windows 2000 network security
technologies are interdependent
- When your Internet connection is in place, the first
community of users to address when you deploy an overall
network security strategy is the group previously defined as
Everyone.
- You should also consider the network applications that
Everyone can benefit from and the security requirements
those applications have.
- People in the Staff group might want to access the
corporate network from any location - primary security goal
in these cases is to verify that the user is an authorized
employee before the user gains free access to the network.
- Employees can use Internet service providers to access
the company network; however, you might not want to make all
intranet services available through the Internet –
therefore, you need to define remote access policies that
are highly specific
To determine what levels of
security are required:
- Create information and communication scenarios that
reflect the types of information you must protect and the
flow of information between entities on your networks.
- Determine the security levels that are required for each
scenario.
- Define the technical requirements for meeting the
security goals.
Single Sign-On VS Two-Factor
Authentication
SSO
Two-factor authentication
- Requires users to present a physical object that encodes
their identities plus a password.
- Common examples of two-factor authentication: automated
teller machine requires a personal identification number in
addition to the card, biometric identification requires the
scanning of the user's handprint, thumbprint, iris, retina,
or voiceprint in place of an access card, in addition to a
password.
- Windows 2000 supports the use of smart card for
two-factor authentication
Case Studies
Below are the links to some case studies. You should go
through them and make yourself familiar with the way their
stories are structured. Look at how Microsoft interprets these
cases. Know what are considered as the best options for each
case.
"Manufacturing is the primary business of this
organization. Product assembly takes place at numerous
locations in North America; however, their business offices
are located all over the world, creating a highly distributed
global computing environment. There are several primary
product divisions with multiple product lines. The numerous
internal teams distributed worldwide require diverse levels of
access to customer and internal documents. The users in each
division require a high level of client-based customization.
Additionally, there are numerous vendors and subcontractors,
some of whom need network access within the firewall, and
others whose needs require only external access. Network
administrators need to provide varying levels of security
based on the needs of each unique internal and external team."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/deploy/dgaf_map_sdyx.asp
Further Readings on the web
…
Read the best practice articles available in
http://www.microsoft.com/security/ :

Focus your attention on the articles in the following
sections:
- Security Strategies
- Securing and Protecting Networks
Also visit the section “Security Best Practices for IT
Professionals” at
http://www.microsoft.com/technet/treeview/default.asp?url=/technet/security/bestprac/default.asp
These best practices often give you the clue on “which
answer is the best”!
Recommended Books …
MCSE: Windows 2000 Network Security Design Study Guide
Exam 70-220 (With CD-ROM)
by Gary Govanus, Robert King (Hardcover)
MCSE Designing Microsoft Windows 2000 Network Security
Readiness Review; Exam 70-220
by Jeff Durham, MeasureUp Inc. (Paperback)
MCSE Windows 2000 Network Security Design: Training
Guide Exam 70-220 (with CD-ROM)
by Roberta Bragg (Hardcover)
MCSE Designing Security for Windows 2000 Network Study
Guide (Exam 70-220) (Book/CD-ROM package)
by Thomas Shinder (Editor), et al (Hardcover) |