|
Designing a Microsoft Windows 2000 Network
Infrastructure When you pass this exam, you
achieve Microsoft Certified Professional status. You also earn
credit toward the following certifications:
Elective credit toward Microsoft Certified Systems Engineer
on Microsoft Windows 2000 certification
According to Microsoft,
"This certification exam tests the skills required to
analyze the business requirements for a network infrastructure
and design a network infrastructure that meets business
requirements. Network infrastructure elements include:
Network topology
Routing
IP addressing
Name resolution such as WINS and DNS
Virtual private networks
Remote access
Telephony solutions
"
The scale of the Windows 2000 environment we are talking
about in this exam are:
- Supported users range from 200-26,000+
- Physical locations range from 5-150+
- Typical network services and applications include file
and print, database, messaging, proxy server or firewall,
dial-in server, desktop management, and Web hosting.
- Connectivity needs include connecting individual offices
and users at remote locations to the corporate network and
connecting corporate networks to the Internet.
It is recommended that you first start by studying 70-215
and 70-216 to ensure that you are familiar with Windows 2000
Active Directory.
This exam is CASE STUDY BASED. You should download and try
the Case Study-Based Test Demo available at
http://download.microsoft.com/download/vb50pro/Update/2.0/W9X2K/EN-US/IIT_Demo.EXE
to become familiar with these new types of questions before
taking the exam.
Your focus on this exam is on
the infrastructure options such as connectivity, routing,
remote access and VPN, as well as some sevurity arrangement.
Remember, the answers, form
our point of view, could appear highly subjective. You need to
choose the BEST answer that fits your case.
Network Infrastructure Elements
Advice from Microsoft:
"While you are documenting your current network
environment, take special note of areas where you are
currently experiencing problems. If you stabilize your network
before deploying a new operating system, deployment and
troubleshooting will be easier, and you can have increased
confidence in the upgraded network. Setting up a test lab to
duplicate problems and configurations is a good way to
evaluate the impact of deploying Windows 2000..."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgbo_nif_ssjx.htm
Documenting your network infrastructure:
- obtaining hardware data to document your
infrastructure's physical structure
- obtaining software data to document the existence and
configuration of the protocols in use
- document the logical organization of your network, name
and address resolution methods, and the existence and
configuration of services used
- also document the location of your network sites and the
available bandwidth between them
As said by Microsoft, "Developing a physical and logical
diagram of your network will help you organize the information
you gather in an understandable and intuitive manner."
Physical Network Diagram presents:
- Details of physical communication links
- Servers, with computer name, IP address (if static),
server role, and domain membership
- Location of devices
- Specifications of devices: firmware version, throughput,
and any special configuration requirements
- WAN communication links and the available bandwidth
between sites
- Number of users at each site, including mobile users.
Logical Network Diagram shows:
- Existing domain hierarchy, names, and addressing scheme.
- Server roles
- Trust relationships
Network Configuration Information that must be collected:
- Name Resolution Services
- IP Service Configurations
- DHCP settings
-
IP Addressing scheme
- Remote and Dial-up Networking
- Current bandwidth utilization
Microsoft Suggested Steps for preparation of the network
infrastructure
- Identify computers that do not have sufficient or
compatible hardware.
- Upgrade hardware.
- Identify computers with software that is not compatible
or that will not operate properly with Windows 2000.
- Identify the applications most often used, so that
compatibility testing is done on all of the most important
applications.
- Analyze network usage to determine network capacity
availability, protocols in use, and which computers are
being used as servers.
- Upgrade incompatible applications.
- Ensure that incompatible applications are not used.
Name Resolution Services
- find out whether any of the DNS servers not running
Windows NT on your network can support dynamic registration
and Service (SRV) resource records
- find out whether upgrades for SRV support are available
from the software manufacturer
- if upgrade not available, may need to replace them – SRV
RR support is a MUST
- for hosts that are not running Windows NT, document the
services they use and provide, such as UNIX BIND – make sure
you document the version of each service in use
- remember, for pure Windows 2000 environment DNS alone is
enough
- when legacy windows computers are present, use WINS
together with DNS
- for DNS, the best type of zone is Active Directory
integrated zone
"The WINS server solves the problems inherent in
resolving NetBIOS names through IP broadcasts, and frees
network administrators from the demands of updating static
mapping files, such as LMHOST files. WINS, which is compliant
with the NetBIOS Name Server (NBNS) RFCs (1001/1002), also
automatically updates the WINS database when dynamic
addressing through DHCP results in new IP addresses for
computers that move between subnets. Neither the user nor the
network administrator needs to make manual accommodations for
such name resolutions."
http://www.microsoft.com/windows2000/techinfo/howitworks/communications/nameadrmgmt/wins.asp
"Active Directory uses DNS as the domain controller
location mechanism, enabling computers to find the IP
addresses of the domain controllers. In order to find a domain
controller in a particular domain or forest, a client queries
DNS for the appropriate service location (SRV) and address (A)
resource records. These DNS resource records provide the names
and IP addresses of the domain controllers. Therefore, the DNS
server used to support Active Directory deployment must
support SRV records. In addition, Microsoft highly recommends
that such DNS servers also support dynamic updates. The domain
controllers dynamically register DNS records necessary for the
successful functionality of the domain controller location
mechanism."
http://www.microsoft.com/technet/treeview/default.asp?url=/technet/prodtechnol/ad/windows2000/deploy/prodspecs/dnsreq.asp
IP Addressing Methods and Service Configurations
- document all the DHCP service servers
- for the clients, know the following:
- default gateway settings
- number of subnets and hosts
- the IP addresses / submasks used
- address leasing configuration
- static IP is a MUST for servers
- static IP is more efficient for small and simple network
- DHCP is a must when your network is complex and when you
do not have enough "real" IP addresses to share
- multiple DHCP server that follows the 80/20 rule can
provide fault tolerance
- you need DHCP relay agent for subnets without DHCP
server
- you should pay attention to supporting BOOTP clients
"Dynamic Host Configuration Protocol (DHCP) is a TCP/IP
standard that reduces the complexity and administrative
overhead of managing network client IP address configuration.
Microsoft® Windows® 2000 Server provides the DHCP service,
which enables a computer to function as a DHCP server and
configure DHCP-enabled client computers on your network. DHCP
runs on a server computer, enabling the automatic, centralized
management of IP addresses and other TCP/IP configuration
settings for your network's client computers."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/cnet/cncb_dhc_IOMJ.asp
"The Bootstrap Protocol (BOOTP) is a computer
configuration protocol developed before DHCP. DHCP improves on
BOOTP and resolves specific limitations BOOTP had as a
computer configuration service. RFC 951 defines BOOTP.
BOOTP was intended to configure diskless workstations
with limited boot capabilities, while DHCP was intended to
configure frequently relocated networked computers (such as
portables) that have local hard drives and full boot
capabilities."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/cnet/cncb_dhc_GCXQ.asp
Remote and Dial-up Networking
- for the remote or mobile users, document the remote
access and dial-up configurations
- call back security is a MUST for RAS users
- for VPN users, document the configuration of VPN
- always remember, L2TP is the best for pure Windows 2000
environment
- when there are non-Windows 2000 computers, use P2TP
- Windows 2000 PPP infrastructure includes support for:
- Dial-up remote access as client
- Dial-up remote access as server
- VPN remote access as client
- VPN remote access as server
- On-demand or persistent dial-up demand-dial routing as
calling router
- On-demand or persistent dial-up demand-dial routing as
answering router.
- On-demand or persistent VPN demand-dial routing as
calling router
- On-demand or persistent VPN demand-dial routing as
answering router.
- RRAS is the Windows 2000 component that provides these
services
- RRAS = Routing + RAS. Why combine both routing and
remote access into a single service?
"The reason for combining the two services lies in the
Point-to-Point Protocol (PPP), which is the protocol suite
that is commonly used to negotiate point-to-point connections
for remote access clients. PPP provides link parameter
negotiation, the exchange of authentication credentials, and
network layer protocol negotiation. For example, when you dial
an Internet service provider (ISP) using PPP, you agree to the
size of the packets you are sending and how they are framed
(link negotiation), you log on using a user name and password
(authentication), and you obtain an IP address (network layer
negotiation). Demand-dial routing connections also use PPP to
provide the same kinds of services as remote access
connections (link negotiation, authentication, and network
layer negotiation). Therefore, the integration of routing
(which includes demand-dial routing) and remote access was
done to leverage the existing PPP client/server infrastructure
that existed for the remote access components."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/intwork/inad_ntr_tzai.asp
- Routing and Remote Access Service
- Static IP routing
- Routing Information Protocol (RIP) versions 1 and 2
- Open Shortest Path First (OSPF)
- DHCP Relay Agent
- Network address translation
- IP packet filtering
- ICMP router discovery
- Multicast forwarding
- Internet Group Management Protocol (IGMP) versions 1 and
2
- Multicast boundaries
- IPX packet filtering
- RIP for IPX
-
SAP for IPX
- NetBIOS over IPX
- Single-path routing infrastructure
- only a single path exists between any two networks in
the internetwork
- simplify the routing tables and the packet flow paths
- not fault tolerant - downed link or a downed router
must be brought back up before packets can be delivered
successfully across the downed link or router.
- Multipath routing infrastructure
- multiple paths exist between networks in the
internetwork
- fault tolerant when dynamic routing is used
- some routing protocols can balance the load of network
traffic across multiple paths
- more complex to configure
- have a higher probability of routing loops during
convergence (when using distance vector-based routing
protocols such as RIP)
Bandwidth
- document your network's current bandwidth utilization to
establish a baseline from which changes can be measured -
you should record available bandwidth during the course of
low, normal, and high network utilization.
- bandwidth metrics include bytes and packets sent or
received, transmit and receive errors, and packets per
second
- document the speed of the network links between the
network segments and the geographical locations- look at the
logical and geographical dispersion in terms of bandwidth
considerations and consider the amount and type of traffic
over your organization's communication links
- If WAN links periodically slowed by domain replication
between domain controllers at different sites, then you may
need to reconsider the site configuration
- also consider to adjust replication settings
- replication over the WAN is always bad
- Microsoft recommends that you "Evaluate bandwidth
demand in your test lab for a specific configuration. For
instance, if your organization plans to carry voice and
video over your data network, your cabling and switches must
be capable of handling the bandwidth demand of those
services."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgbo_nif_xetr.htm
ALWAYS review your network
devices for compatibility with Windows 2000.
Security
"Network security becomes most critical when you connect
your computers to a network that you do not entirely trust.
Network security issues are common within an organization …
Beyond your organization, options for accountability and
discipline are greatly diminished, and therefore you need to
rely more strongly on security strategies themselves."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/deploy/dgfb_emp_PAEL.asp
In fact, you will see security related questions in the
exam. Therefore, it is suggested that you also study the
material for 70-220 before attempting this exam.
PKI is a MUST have for any e-enabled enterprise. How does
PKI work?
"The basic idea of public key cryptography is that there
are two keys that are related. One key can be passed openly
and freely between parties or published in a public
repository; the other key must remain private. There are also
different types of public key algorithms, each with its own
characteristics. This means that it is not always possible to
substitute one algorithm for another. If two algorithms can
perform the same function, the detailed mechanism by which
that result is obtained varies. With public key cryptography,
the two keys are used in sequence. If the public key is used
first, followed by the private key, then this is a key
exchange operation. If the private key is used first, followed
by the public key, this is a digital signature operation."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgch_pki_izmk.htm
Keep in mind that PKI is based on cryptography. It relies
on certificates for authentication.
"Cryptography protects users by providing functionality
for the encryption of data and authentication of other users.
This technology lets the receiver of an electronic message
verify the sender, ensures that a message can be read only by
the intended person, and assures the recipient that a message
has not be altered in transit."
http://www.microsoft.com/WINDOWS2000/techinfo/howitworks/security/cryptpki.asp
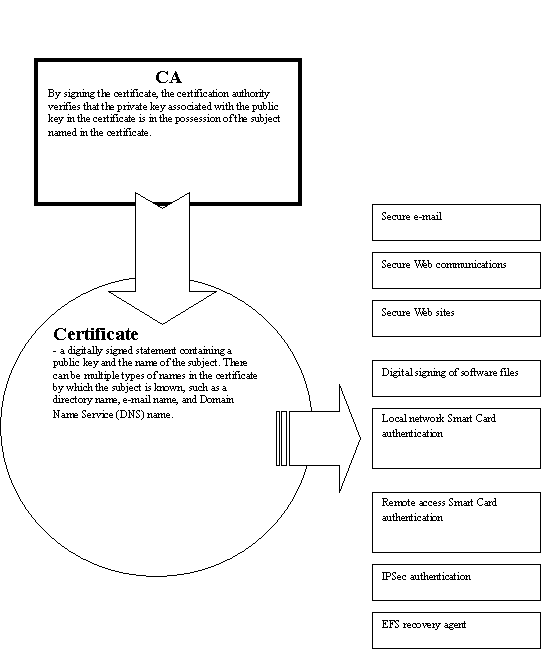
What type of CA should we use? See what Microsoft said:
"A CA hierarchy requires planning. The first business
policy decisions you make will have to do with selecting the
CAs, both internal and external, that will be the source of
your certificates. A typical CA hierarchy has a three-level
architecture. It is recommended that you have one root CA, and
that it be offline. You need a second level of CAs to
implement certificate policy. This level also needs to be
offline. The third level is the issuing CAs. You can have
internal or external CAs at this level. Internal network
authentication and data integrity can be handled by a local
certifying authority, such as your IT department. Internet
transactions and software signing might require third-party
certificates in order to establish public credibility. While
selecting your CAs, give some thought to your cryptographic
service provider (CSP). The CSP is the software or hardware
that provides encryption services for your CA."
http://www.microsoft.com/WINDOWS2000/techinfo/reskit/en/Deploy/dgch_pki_kvsq.htm
Steps to take for setting up certification authorities:
- Plan a certification hierarchy
-
Set up a Windows 2000 Server for each
certification authority
- Plan the renewal strategy you are going to use for the
root certification authority
-
Install a root certification authority
- Install subordinate certification authorities as
required by your planned certification hierarchy
- Install Web enrollment services on non-certification
authority servers, as required.
Configuration for each certification authority:
- Specify whether to make each incoming certificate
request pending or automatically approved
- Schedule the publication of the certificate revocation
list
- Set up applications and services to use your public key
infrastructure
- Set up a Web server to use certificates for secure
access Certificates and Internet Information Services
- Set up Internet Protocol security - IPSec
-
Set up a Microsoft Exchange server to use
certificates for secure e-mail
Migration
"Migrating successfully from Microsoft® Windows NT® 3.51
and Microsoft® Windows NT 4.0 to Microsoft® Windows® 2000
requires careful analysis of your current system and in-depth
planning."
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/deploy/dgbf_upg_XSAF.asp
Some of the questions you encounter will involve migration
and upgrade issue. Therefore, it is suggested that you also
study the material for 70-222 before attempting this exam.
Reference Books:
MCSE Designing a Windows 2000 Network Study Guide (Exam
70-221)
by Thomas Shinder (Editor), et al (Hardcover)
MCSE Designing a Microsoft Windows 2000 Network
Infrastructure Readiness Review; Exam 70-221
by Emmett A. Dulaney, MeasureUp Inc. (Paperback)
Test Yourself MCSE Designing A Windows 2000 Network
(Exam 70-221)
by John M. Gunson II (Editor) (Paperback)
MCSE Training Guide (70-221): Designing a Windows 2000
Network Infrastructure
by Dale Holmes, et al (Hardcover) |