|
Installing, Configuring, and Administering Microsoft®
Internet Security and Acceleration (ISA) Server 2000,
Enterprise Edition This exam tests your ability to
implement, administer, and troubleshoot information systems
that incorporate the Enterprise Edition of Microsoft Internet
Security and Acceleration Server 2000. The focus is on the
Enterprise Edition, although in a standalone setup there is
really no difference between the Enterprise edition and the
Standard edition.
The characteristics of the expected scenario, according to
Microsoft, are:
n
Between 200 and 26,000+ supported users
n
Multiple physical locations
n
Outbound access for typical client services and
applications, such as Web access, e-mail, Telnet, FTP, virtual
private networking (VPN), desktop management, and access
control policies
n
Hosting of network services, such as internal
and external Web hosting, messaging, and firewall
n
Connectivity needs that include connecting
individual offices and users at remote locations to the
corporate network and connecting corporate networks to the
Internet
When you pass this exam, you can achieve Microsoft
Certified Professional status. You also earn credit toward the
following certifications:
n
Elective credit toward Microsoft Certified
Systems Administrator on Microsoft Windows 2000 certification
n
Elective credit toward Microsoft Certified
Systems Engineer on Microsoft Windows 2000 certification
Deployment Planning Considerations:
Before your Microsoft Internet Security and Acceleration
(ISA) Server deployment, the factors below should be planned
for:
n
Network size - how many ISA Server computers to
deploy?
n
Array considerations - how to map your ISA
servers into arrays?
n
ISA Server mode - firewall, cache, or
integrated?
n
ISA Server installation options - whole package
or specific options?
n
User needs - what applications and services do
your users require?
n
Internet connectivity requirements - how you
will physically connect your internal network to the Internet?
System
Requirements and Capacity Planning
The minimum non-sense requirements to use ISA Server are:
n
300 MHz or higher Pentium II-compatible
processor
n
256 MB of RAM
n
20 MB free hard-disk space
n
One network adapter (as a firewall, you better
have at least 2)
The OS requirement:
n
Windows 2000 Server with Service Pack 1 or
later, OR
n
Windows 2000 Advanced Server with Service Pack 1
or later, OR
n
Windows 2000 Datacenter Server
Other requirement:
n
For array and advanced policies, you need to
have Windows 2000 Active Directory running on your network.
n
To remotely manage ISA Server, you only need to
install ISA Management client.
The Microsoft suggested hardware capacity for providing
caching:
|
User base |
Processor |
Memory |
Disk space for caching |
| Up
to 500 |
Pentium II, 300 MHz |
256 MB |
2-4 GB |
| 500
- 1,000 |
Pentium III, 550 MHz |
256 MB |
10 GB |
|
More than 1,000 |
Two
ISA Server computers with Pentium III, 550 MHz |
256
for each server. |
10 Gigabytes for each server. |
The Microsoft suggested hardware capacity for publishing
your internal servers:
|
Hits/second |
Processor |
|
Less than 800 |
Pentium II, 300 Megahertz (MHz) |
|
Approximately 800 |
Pentium III, 550 MHz |
|
More than 800 |
Pentium III, 550 MHz. For each 800 hits per second, add an
ISA Server computer or add more processors to the ISA
Server computer. |
ISA Server Operating Modes
|
Feature |
Firewall Mode
|
Cache Mode
|
Integrated Mode |
|
Enterprise policy |
Yes |
Yes |
YES |
|
Access policy |
Yes |
HTTP only |
YES |
| Web
publishing |
Yes |
Yes |
YES |
|
Server publishing |
Yes |
No |
YES |
|
Packet filtering |
Yes |
No |
YES |
|
Cache configuration |
No |
Yes |
YES |
|
Application filters |
Yes |
No |
YES |
| Web
filters |
Yes |
Yes |
YES |
|
Real-time monitoring |
Yes |
Yes |
YES |
|
Alerts |
Yes |
Yes |
YES |
|
Reports |
Yes |
Yes |
YES |
|
Virtual private networking |
Yes |
No |
YES |
|
SecureNAT client support |
Yes |
No |
YES |
|
Firewall client support |
Yes |
No |
YES |
| Web
Proxy client support |
Yes |
Yes |
YES |
ISA Client Types
This information is
provided by the ISA Server documentation:
|
Feature |
SecureNAT client |
Firewall client |
Web Proxy client |
|
Installation required |
Some network configuration changes are required |
Yes |
No,
requires Web browser configuration |
|
Operating system support |
Any
operating system that supports TCP/IP |
Only Windows platforms |
All
platforms, but by way of Web application |
|
Protocol support |
Requires application filters for multi-connection
protocols |
All
Winsock applications |
HTTP
HTTPSFTP
Gopher |
|
User-level authentication |
Some network configuration changes are required |
Yes |
Yes |
|
Server applications |
No
configuration or installation required |
Requires configuration file |
N/A |
The following information is extracted from the author
Michael Yu Chak Tin's SANS GCFW practical. His entire posted
practical is available soon for download at
http://www.giac.org/GCFW.php.
According to Microsoft,
"Microsoft Internet Security and Acceleration (ISA)
Server 2000 is an extensible enterprise firewall and Web cache
server that integrates with the Microsoft Windows 2000
operating system for policy-based security, as well as
accelerating and managing internetworking. ISA Server provides
two tightly integrated modes-a multilayer firewall and a
high-performance Web cache server. The firewall provides
filtering at the packet, circuit, and application layer,
stateful inspection to examine data crossing the firewall,
control of access policy, and routing of traffic. The cache
improves network performance and enhances the end-user
experience by storing frequently requested Web content. The
firewall and cache can be deployed separately on dedicated
servers or integrated on the same computer."
The reason ISA Server is deployed in a network can include:
n
enhance performance - it can act as a proxy
caching server for the internal clients, thus enhancing the
client's internet browsing performance
n
protect - it has advanced stateful inspection
technology for protecting the network
n
publish - reverse proxying and protection for
the internal servers
First of all, install the latest service pack. At the time
of this writing, SP2 is the latest available version. In fact,
ISA will not install unless you have applied SP1 at the least.
Microsoft offers Windows 2000 service packs via this URL:
http://www.microsoft.com/windows2000/downloads/servicepacks/default.asp
Additionally, the security updates available at
http://www.microsoft.com/windows2000/downloads/security/default.asp
should be applied.
ISA Server includes a Security Configuration Wizard for
hardening the Windows 2000 installation. Before invoking ISA
for this purpose, apply all the available service packs and
updates.
Available at
http://www.microsoft.com/isaserver/downloads/sp1.asp,
"Internet Security and Acceleration (ISA) Server 2000
Service Pack 1 (SP1) provides the latest updates to ISA Server
and provides an even higher level of reliability and stability
to customers. Microsoft strongly encourages customers to
install SP1 on all computers running ISA Server."
According to Microsoft, ISA Server SP1 includes all hot
fixes issued since ISA Server was released to manufacturing,
fixes for common issues reported by customers through
Microsoft Product Support Services (PSS) as well as fixes
recommended through an audit by third-party security experts.
Once the service pack is applied, we can invoke the
Security Configuration Wizard and start hardening Windows 2000
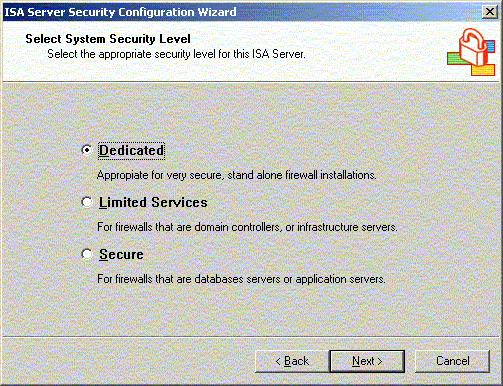
Server. Of the three different security levels, choose
"Dedicated" to produce the most secure firewall system.
The Proxy and Caching functions
A proxy server is a server that sits between a client
application and a real server that intercepts all requests to
the real server to see if it can fulfill the requests itself.
As described by Webopedia.com, proxy servers have two main
purposes:
"Improve Performance: Proxy servers can dramatically
improve performance for groups of users. This is because it
saves the results of all requests for a certain amount of
time. Consider the case where both user X and user Y access
the World Wide Web through a proxy server. First user X
requests a certain Web page, which we'll call Page 1. Sometime
later, user Y requests the same page. Instead of forwarding
the request to the Web server where Page 1 resides, which can
be a time-consuming operation, the proxy server simply returns
the Page 1 that it already fetched for user X. Since the proxy
server is often on the same network as the user, this is a
much faster operation. Real proxy servers support hundreds or
thousands of users. The major online services such as
Compuserve and America Online, for example, employ an array of
proxy servers.
Filter Requests: Proxy servers can also be used to
filter requests. For example, a company might use a proxy
server to prevent its employees from accessing a specific set
of Web sites."
Policy Confusion
ISA Server supports dynamic filtering, meaning ports are
opened and closed on an on-demand basis. At the same time, ISA
Server supports packet filtering, which is static in nature.
So, what is the difference? Somehow most ISA Server
documentations out there fail to clearly explain the
difference.
In fact, ISA Server provides security via the following
means:
n
Access Policy -> Protocol Rules - allow internal
client access to the Internet. This is dynamic in nature.
n
Access Policy -> Packet filtering rules - open
or close port statically.
n
Publishing Rules - allow external clients access
to internal servers. This is dynamic in nature as well.
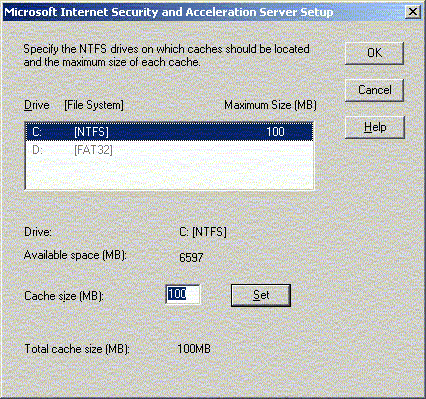
The default cache size is 100MB. This may not be enough.
The factors to consider include the number of users and the
frequency of use.
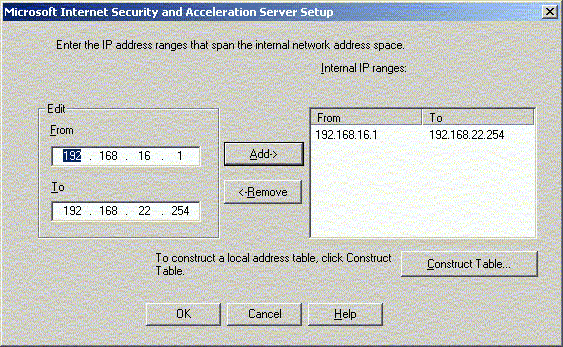
LAT
Keep in mind, the construction of this LAT (Local Address
table) is very important, as ISA Server relies solely on it to
distinguish between trusted nodes and untrusted nodes. If
there are changes to the IP address settings, this LAT must be
reconstructed. And since the construction of LAT relies
heavily on information provided by the routing table, you must
ensure that there is no invalid routing entry. Using automatic
mechanism like RIP eliminates the need for manually changing
the routing table.
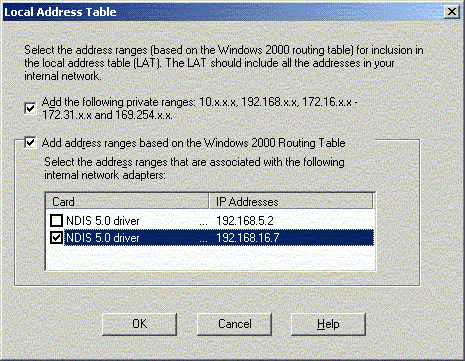
Only include the local interface in the LAT. Do not include
the internet interface, or ISA will mis-behave.
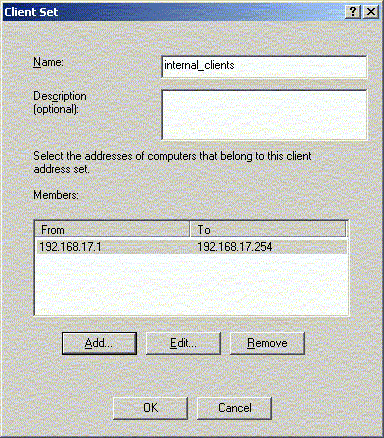
The internal clients should be properly defined as client
sets.
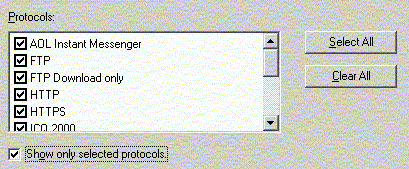
Protocol rules in ISA Server determine which protocols
clients can use to access the internet. The protocols that the
users use must be carefully selected. Rules are applied to
allow outbound requests only on these protocols.
These protocols are application specific. For example, AOL
Messenger and ICQ use different protocols. Whether or not
these applications are allowed is a matter of company policy.
ISA Server relies on packet filtering for its firewall
functionalities. Packet filtering, intrusion detection and IP
routing can be enabled. To be secure, all packet filtering and
intrusion detection related options should be enabled as well.
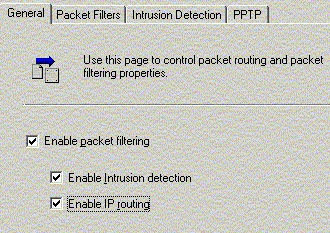
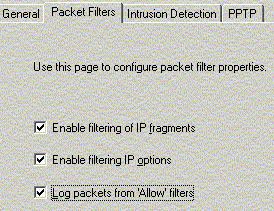
For packet filtering, the single most important setting
is to deny any requests towards the internal network made by
any outside parties. Absolutely no connection initiated from
the outside! This can be done by creating "block filter" that
stop the external hosts from sending packets to all ports on
the ISA Server computer.
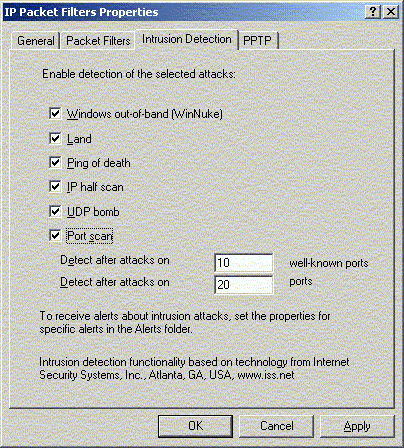
Since your internal clients may be acting as remote VPN
clients for accessing the partners' VPN servers, outgoing PPTP
traffic should be allowed to pass through the firewall.
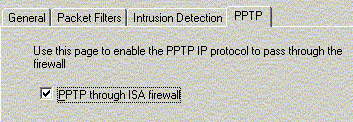
To allow room for scalability, multiple ISA servers can be
chained to form a larger caching mechanism. You can determine
if you should ensure that all requests are immediately routed
to the destinations rather than to any upstream cache servers,
and whether the HTTP / SSL protocols should be transformed
into another format when the requests are processed by ISA
server.
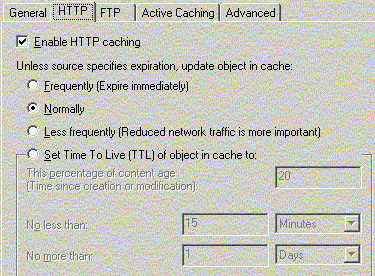
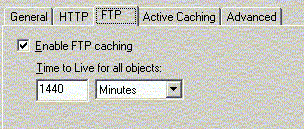
ISA Server supports two major types of caching: HTTP and
FTP. There is always a tradeoff between network traffic and
content updates. If the cached objects are to be kept in the
cache for a longer period of time, performance will increase
because less outgoing traffic is required. However, the cached
objects may become outdated. The settings can be adjusted in
the form of TTL. As described by Webopedia.com,
"Short for Time to Live, (TTL is) a field in the
Internet Protocol (IP) that specifies how many more hops a
packet can travel before being discarded or returned."
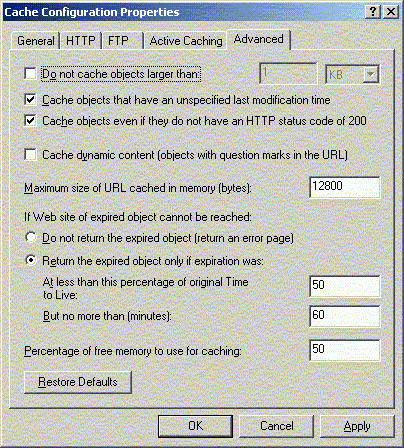
As mentioned before, cached objects may be outdated. For
certain objects that involve dynamic contents, caching can be
a bad idea. Therefore, do not enable the option "Cache Dynamic
Content" for very dynamic contents.
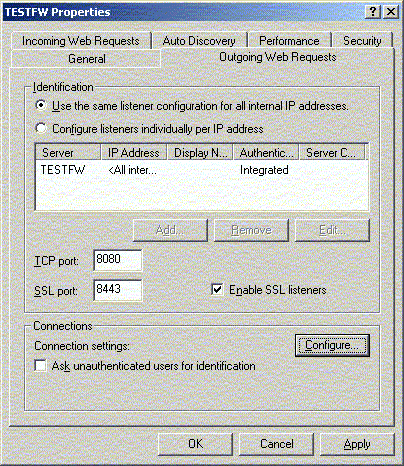
A default configured ISA server will listen on TCP port
8080 as well as SSL port 8443 (SSL port listener must be
manually enabled) for outgoing requests. The clients must be
configured to forward requests to these ports of the ISA
Server's internal interface.
You may prevent unauthorized users to access your proxy
ports by configuring input filters to allow connections to be
made to TCP 8080 and 8443 only from you're your internal
clients. You do want to ensure that no one from the outside
can make use of your proxy functions.
Web Publishing
Web publishing rules
n
determine how ISA Server should intercept
incoming requests for HTTP objects on an internal Web server
n
determine how ISA Server should respond on
behalf of the Web server
n
all requests are forwarded downstream to the
internal Web server behind the ISA Server
n
internal Web server cannot require digest or
basic authentication or the internal name and IP address of
the Web server may be exposed
Destination sets and client sets
n
destination sets usually include the external
name of your ISA Server computer
n
client address sets should include IP addresses
of clients located on the Internet
Action
n
request can be:
u
honored
u
discarded
u
redirected to an alternate site
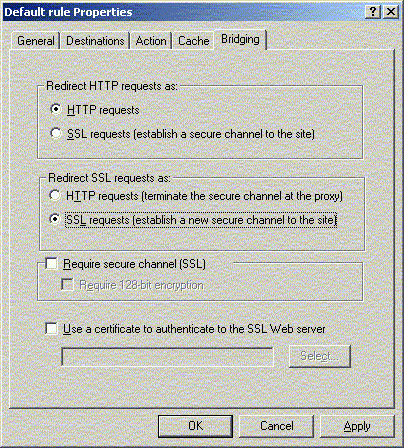
Bridging
n
determine how SSL requests should be redirected:
u
as HTTP requests
u
as SSL requests
n
when requests are redirected as SSL requests,
the redirection is referred to as SSL bridging
n
You can secure HTTP communication by having it
redirected using SSL
n
You can configure HTTP or SSL requests to be
passed on as an FTP request to the internal Web server
Rule processing
n
Web publishing rules are processed in order
n
If no rule matches, ISA Server processes the
default rule
n
The default rule is configured to discard all
requests
n
The default rule is last in the order
Port Settings
To be able to properly protect the network without
restricting the functionality, you must know the types of
traffic in the network.
You must be
able to tell what port to block or allow when the exam
question asks you to watch out for a particular problematic
application.
The list below is provided by Microsoft at
http://www.microsoft.com/windows2000/techinfo/reskit/en-us/default.asp?url=/WINDOWS2000/techinfo/reskit/en-us/cnet/cnfc_por_simw.asp
:
|
Service Name |
UDP |
TCP |
|
Browsing datagram responses of NetBIOS over TCP/IP |
138 |
|
|
Browsing requests of NetBIOS over TCP/IP |
137 |
|
|
Client/Server Communication |
|
135 |
|
Common Internet File System (CIFS) |
445 |
139, 445 |
|
Content Replication Service |
|
560 |
|
Cybercash Administration |
|
8001 |
|
Cybercash Coin Gateway |
|
8002 |
|
Cybercash Credit Gateway |
|
8000 |
|
DCOM (SCM uses udp/tcp to dynamically assign ports for
DCOM) |
135 |
135 |
|
DHCP client |
|
67 |
|
DHCP server |
|
68 |
|
DHCP Manager |
|
135 |
|
DNS Administration |
|
139 |
|
DNS client to server lookup (varies) |
53 |
53 |
|
Exchange Server 5.0 |
|
|
|
Client Server Communication |
|
135 |
|
Exchange Administrator |
|
135 |
|
IMAP |
|
143 |
|
IMAP (SSL) |
|
993 |
|
LDAP |
|
389 |
|
LDAP (SSL) |
|
636 |
|
MTA - X.400 over TCP/IP |
|
102 |
|
POP3 |
|
110 |
|
POP3 (SSL) |
|
995 |
|
RPC |
|
135 |
|
SMTP |
|
25 |
|
NNTP |
|
119 |
|
NNTP (SSL) |
|
563 |
|
File shares name lookup |
137 |
|
|
File shares session |
|
139 |
|
FTP |
|
21 |
|
FTP-data |
|
20 |
|
HTTP |
|
80 |
|
HTTP-Secure Sockets Layer (SSL) |
|
443 |
|
Internet Information Services (IIS) |
|
80 |
|
IMAP |
|
143 |
|
IMAP (SSL) |
|
993 |
|
IKE (For more information, see Table C.4) |
500 |
|
|
IPSec Authentication Header (AH) (For more information,
see Table C.4) |
|
|
|
IPSec Encapsulation Security Payload (ESP) (For more
information, see Table C.4) |
|
|
|
IRC |
|
531 |
|
ISPMOD (SBS 2nd tier DNS registration wizard) |
|
1234 |
|
Kerberos de-multiplexer |
|
2053 |
|
Kerberos klogin |
|
543 |
|
Kerberos kpasswd (v5) |
464 |
464 |
|
Kerberos krb5 |
88 |
88 |
|
Kerberos kshell |
|
544 |
|
L2TP |
1701 |
|
|
LDAP |
|
389 |
|
LDAP (SSL) |
|
636 |
|
Login Sequence |
137, 138 |
139 |
|
Macintosh, File Services (AFP/IP) |
|
548 |
|
Membership DPA |
|
568 |
|
Membership MSN |
|
569 |
|
Microsoft Chat client to server |
|
6667 |
|
Microsoft Chat server to server |
|
6665 |
|
Microsoft Message Queue Server |
1801 |
1801 |
|
Microsoft Message Queue Server |
3527 |
135, 2101 |
|
Microsoft Message Queue Server |
|
2103, 2105 |
|
MTA - X.400 over TCP/IP |
|
102 |
|
NetBT datagrams |
138 |
|
|
NetBT name lookups |
137 |
|
|
NetBT service sessions |
|
139 |
|
NetLogon |
138 |
|
|
NetMeeting Audio Call Control |
|
1731 |
|
NetMeeting H.323 call setup |
|
1720 |
|
NetMeeting H.323 streaming RTP over UDP |
Dynamic |
|
|
NetMeeting Internet Locator Server ILS |
|
389 |
|
NetMeeting RTP audio stream |
Dynamic |
|
|
NetMeeting T.120 |
|
1503 |
|
NetMeeting User Location Service |
|
522 |
|
NetMeeting user location service ULS |
|
522 |
|
Network Load Balancing |
2504 |
|
|
NNTP |
|
119 |
|
NNTP (SSL) |
|
563 |
|
Outlook (see for ports) |
|
|
|
Pass Through Verification |
137, 138 |
139 |
|
POP3 |
|
110 |
|
POP3 (SSL) |
|
995 |
|
PPTP control |
|
1723 |
|
PPTP data (see Table C.4) |
|
|
|
Printer sharing name lookup |
137 |
|
|
Printer sharing session |
|
139 |
|
Radius accounting (Routing and Remote Access) |
1646 or 1813 |
|
|
Radius authentication (Routing and Remote Access) |
1645 or 1812 |
|
|
Remote Install TFTP |
|
69 |
|
RPC client fixed port session queries |
|
1500 |
|
RPC client using a fixed port session replication |
|
2500 |
|
RPC session ports |
|
Dynamic |
|
RPC user manager, service manager, port mapper |
|
135 |
|
SCM used by DCOM |
135 |
135 |
|
SMTP |
|
25 |
|
SNMP |
161 |
|
|
SNMP Trap |
162 |
|
|
SQL Named Pipes encryption over other protocols name
lookup |
137 |
|
|
SQL RPC encryption over other protocols name lookup |
137 |
|
|
SQL session |
|
139 |
|
SQL session |
|
1433 |
|
SQL session |
|
1024 - 5000 |
|
SQL session mapper |
|
135 |
|
SQL TCP client name lookup |
53 |
53 |
|
Telnet |
|
23 |
|
Terminal Server |
|
3389 |
|
UNIX Printing |
|
515 |
|
WINS Manager |
|
135 |
|
WINS NetBios over TCP/IP name service |
137 |
|
|
WINS Proxy |
137 |
|
|
WINS Registration |
|
137 |
|
WINS Replication |
|
42 |
|
X400 |
|
102 |
Reference Books
MCSE Training Guide (70-227): Installing,
Configuring, and Administering Microsoft Internet Security and
Acceleration (ISA) Server 2000
By Roberta Bragg; Hardcover
MCSE ISA Server 2000 Exam Cram (Exam: 70-227)
By Diana Bartley, Gregory Smith; Paperback
MCSE: ISA Server 2000 Administration Study Guide: Exam
70 227 with CDROM
By William Heldman; Hardcover |